CrowdSec: An introduction

In a world where cyberattacks have become commonplace, it is critical to operate a robust security infrastructure that reliably protects systems and data. CrowdSec is a security tool that helps businesses and organizations protect themselves from cyberattacks by detecting suspicious activity on websites and servers and automatically blocking potential attackers.
The CrowdSec Project
CrowdSec is an open-source security project supported by a community of developers that can be used on a variety of platforms and operating systems. It uses a combination of behavioral analysis and human intelligence to provide accurate threat detection. Through the collaboration of CrowdSec users worldwide, new types of attacks are also quickly detected and blocked.
Accordingly, the CrowdSec application is classified as an intrusion prevention system (IPS for short).
IPS Origins
The origins of IPS date back to the early days of the Internet, when threats such as malware and hacker attacks were becoming more common. One of the best-known IPS solutions is Fail2Ban, an open-source program originally developed in 2004 by Cyril Jaquier. Fail2Ban detects such network attacks by monitoring the server's log files and automatically blocking network access from that source to the system for a specified time.
By locking out an attacker at the network level after a short period of time, IPS technologies such as Fail2Ban and CrowdSec are instrumental in minimizing the effectiveness of digital attacks.
CrowdSec Innovations
Compared to Fail2Ban, CrowdSec brings a number of innovation capabilities that have the potential to again significantly improve effectiveness and efficiency.
One of CrowdSec's most important innovations is its ability to access data from a variety of sources, including public databases and user feeds. This allows the software to detect and block threats on a global scale, rather than being limited to local data. So, (anonymized) IP data from all CrowdSec users worldwide is aggregated and delivered to all users based on the trustworthiness of the data source. Now, attacker IP addresses on systems protected by CrowdSec are blocked before they can connect to the system for the first time. This adds a proactive component to Fail2Ban's reactive approach with CrowdSec, further enhancing system security.
The proactive blocking of IP addresses classified as malicious also drastically limits one of the most important resources available to attackers. Attackers only have a limited number of IP addresses, and once they are all known and proactively blocked, attackers can only do limited damage to systems running CrowdSec. The CrowdSec project describes the goal of outnumbering attackers, as there are significantly more CrowdSec users than attackers.
Another advantage over Fail2Ban is the Collections used by CrowdSec. Collections allow users to uniformly define, share and exchange rules and scenarios for threat detection on their network or IT infrastructure. In addition, CrowdSec provides a central platform for sharing these Collections. The CrowdSec community provides a wide variety of pre-built collections.
Since CrowdSec was already programmed with the Collections functionality in mind, Collections can be quickly and easily added to CrowdSec and kept up to date fully automatically. This functionality was not provided for in Fail2Ban and comparable systems, and can therefore only be implemented with a great deal of manual effort. This is another argument for using or switching to CrowdSec.
CrowdSec Functionality
In this section, we will go into more detail about how CrowdSec works. To illustrate, let's look at the graphic below:
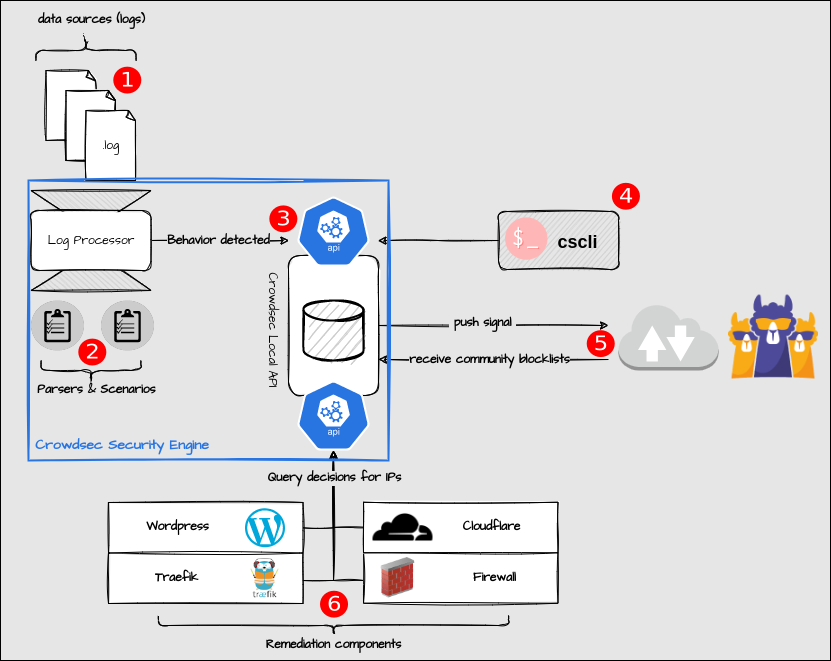
Explanation:
- The CrowdSec Log Processor accesses the log files available in the system. They serve as the data basis for all further steps. (Log files are a kind of "logbook" in which a system or an application logs all activities).
- In the Log Processor, the log files are now parsed ("translated" into a machine-readable form) and compared with predefined threat scenarios. These scenarios are collected and organized in so-called collections.
- If a breach is detected, or more precisely, if a log entry matches one of the installed scenarios, this is reported to the local CrowdSec database via the local CrowdSec API and stored here.
- Using the cscli (CrowdSec CLI) command line tool installed with the software, system administrators can manually access this database, view, modify or add entries.
- IP addresses that trigger a scenario multiple times are automatically reported to CrowdSec. At the same time, CrowdSec provides a list of all IP addresses reported as malicious by the community to us.
- Remediation Components (Application Bouncers) can now be installed on the system, which connect to other applications connected to the Internet. These regularly query the CrowdSec database for blocked IP addresses and block network requests to the application from these sources fully automatically.
Comparison to IP list providers
Finally, a brief comparison between Crowdsec and the providers of lists of conspicuous IP addresses. Keeping IP lists has become a lucrative business model for companies working in the IT security field. Many rely on honeypot systems that are placed on the Internet (sometimes with deliberately built-in security flaws) to identify malicious actors or their IP addresses. CrowdSec also aggregates data from comparable sources, but additionally has the (anonymized) data of all its users. So while IP list providers have a few hundred or a few thousand honeypots in operation, CrowdSec can access data from tens of thousands of endpoints. The CrowdSec data comes almost exclusively from systems in production use, while honeypot data is more synthetic in nature. Some more common honeypot solutions are also automatically detected by attackers and unfortunately lose any usefulness for these specific cases.
In summary, CrowdSec has a larger amount of data with content from productive use. Accordingly, the use of CrowdSec is more suitable for most use cases, especially for SMEs and small businesses, than the offerings of specialized providers.
Comparison with proprietary IPS solutions
CrowdSec also has some advantages in direct comparison to proprietary providers. Firstly, the source code of open source software is publicly available and can be reviewed, improved and adapted by the community. This means that bugs and vulnerabilities can be discovered and fixed more quickly, leading to greater security and stability. Because CrowdSec is open source, it can be deployed without paying expensive licensing fees, making it generally less expensive to deploy. This is especially beneficial for smaller companies or organizations with limited budgets that cannot afford expensive proprietary solutions. Since CrowdSec can be deployed by anyone interested, regardless of individual budget, CrowdSec will always be able to draw on more attack detection data to better protect a system. Finally, with open source software, there is no lock-in to a specific vendor or supplier. This means that businesses and organizations have more flexibility and control over their IT infrastructure and are not reliant on a particular vendor.
Overall, an open source IPS like CrowdSec offers many advantages over a proprietary version from a paid vendor, including higher security, stability, flexibility and lower overall cost.
Use of CrowdSec
CrowdSec Agent can be installed on all major Linux distributions, FreeBSD and Windows. Furthermore, CrowdSec offers support for all common reverse proxies. At this time (as of April 2023), packages are available for integration with PHP. Support for other programming languages will follow soon.
We will go into detail about the installation and actual use of CrowdSec in further blog posts to follow.
Would you like to learn more about CrowdSec, or do you need support with the integration into your infrastructure?
Kyoox offers various services in the cybersecurity area and around CrowdSec. We support you on request from the conceptual planning to the concrete implementation on your infrastructure and with the maintenance of CrowdSec.
Interested? Then contact us now.

